11 KiB
Directory of forges
Whitelist
The following forges have no significant ethical issues:
| forge | registration publicly open | software | Tor-hostile | Cloudflare MitM | forced re/hCAPTCHA | forced execution of non-free software | notes |
|---|---|---|---|---|---|---|---|
| git.fsfe.org | ✅ | Gitea | n | n | n | n | Access intended only for FSFE projects and very small projects; SSH port: 22 |
| git.fuwafuwa.moe(onion) | ✅ | Gitea 1.13.6 | n | n | n | n | SSH port: 22; SSH over Tor broken; HTTPS over Tor works; onion site down lately (maybe they have an onion v3 address now?) |
| dev.sum7.eu | ✅ | Gitea 1.14.0⚠ | n | n | n | n | |
| git.eta.st | ✅ | Gitea 1.15.0⚠ | n | n | n | n | |
| git.slashdev.space | ✅ | Gitea 1.15.4⚠ | n | n | n | n | SSH port: 22; SSH over Tor broken (try HTTPS over Tor) |
| forge.april.org | ❌ | Gitea 1.15.6⚠ | n | n | n | n | French is the primary language; no registration form; access is for April members -- but perhaps April membership is open to all? |
| git.disroot.org | ✅ | Gitea 1.15.6⚠ | n | n | n | n | SSH over Tor works; based in NL |
| git.nixnet.services | ❌ | Gitea 1.15.6⚠ | n | n | n | n | formerly git.nixnet.xyz |
| git.nogafam.es(onion) | ✅ | Gitea 1.15.6⚠ | n | n | n | n | SSH disabled; large repos are git-inaccessible over Tor; onion site is down |
| git.safemobile.org | ✅ | Gitea 1.15.6⚠ | n | n | n | n | |
| opendev.org | ✅ | Gitea 1.15.6⚠ | n | n | n | n | SSH port: 22 |
| try.gitea.io | ✅ | Gitea 1.16.0 | n | n | n | n | Intended only for Gitea experimentation; no expectation of future availability |
| git.pofilo.fr | ❌ | Gitea 1.16.1 | n | n | n | n | no registration link |
| framagit.org | ✅ | Gitlab (CE 13.10.2) | n | n | n | n | may become more restricted in mid-2021 |
| git.jami.net | ✅ | Gitlab (CE) | n | n | n | n | possibly restricted to Jami efforts; acces to help page blocked to non-members so CE/EE unknown |
| git.stuxhost.com | ✅ | Gitlab (CE) | n | n | n | n | |
| gitlab.gnome.org | ✅ | Gitlab (CE) | n | n | n | n | possibly restricted to Gnome efforts |
| gitlab.tails.boum.org | ✅ | Gitlab (CE) | n | n | n | n | possibly restricted to Tails efforts but no AUP says otherwise |
| gitlab.torproject.org | ✅ | Gitlab (CE) | n | n | n | n | open registration; repo creation possibly restricted; Google reCAPTCHA is allegedley used, but not at registration time |
| mypdns.org | ✅ | Gitlab (CE) | n | n | n | n | Home of the deCloudflare project; Gitlab CE assumed (due to being a low-budget service -- plz correct or raise issue if needed) |
| source.small-tech.org | ❌ | Gitlab (CE) | n | n | n | n | |
| notabug.org(onion) | ✅ | Gogs | n | n | n | n | based on liberated fork of Gogs; supports Tor (the onion web UI is currently disabled in response to attack but the onion site accepts git connections); supports SSH keys and SSH over Tor to NAB's onion service; no e-voting; NAB doesn't associate PGP keys to users, so PGP signed commits may be unavailable or more manual work needed. |
| launchpad.net | ✅ | Launchpad | n | n | n | n | It's unknown whether it functions without JavaScript; no wiki |
| gitee.com | ✅ | OSCHINA | n | n | n | n | based in China; registration over Tor with throwaway email works; no automatic mirror (unlike Gitea); some areas written in simplified chinese |
| code.netlandish.com | ❌ | Sourcehut | n | n | n | n | Access restricted to staff of the company working on the hosted projects |
| sr.ht | ✅ | Sourcehut | n | n | n | n | javascript-free; supports patches sent by email; offers an IRC bouncer; recognizes the harm of Cloudflare and takes an ethical stance against it |
Graylist
These forges are not as seriously flawed as the blacklisted ones, but they should still be avoided if possible. Non-Cloudflare sites that use a Cloudflare NS server pose a risk for disruptions because they can trivially and spontaneously flip a switch and route all your traffic through Cloudflare, potentially cutting access to some of your contributors. Dead sites are also graylisted because if they come back online, they are known to be unreliable. Codeberg is graylisted for falsely accusing a repository of illegal conduct and deleting the content of all forks from that project without evidence or redress.
| forge | registration publicly open | software | Tor-hostile | Cloudflare MitM | forced re/hCAPTCHA | forced execution of non-free software | notes |
|---|---|---|---|---|---|---|---|
| (onion) | ❌ | n | n | n | n | dead site | |
| git.passageenseine.fr | ❌ | Gitea | n | n | n | n | dead site |
| gitea.shuishan.net.cn | ❌ | Gitea | n | n | n | n | dead site |
| yerbamate.dev | ❌ | Gitea | n | n | n | n | dead site |
| de.edumat.io | ❌ | Gitea 1.5.2 | n | n | n | n | dead site; no SSH |
| git.teknik.io | ❌ | Gitea 1.9.0 | n | n | n | n | Cloudflare NS server (they can route all traffic via CF at the flip of a switch) |
| gitea.it | ✅ | Gitea 1.12.4 | n | n | n | n | Cloudflare NS server (they can route all traffic via CF at the flip of a switch) |
| git.kiwifarms.net | ✅ | Gitea 1.13.1 | n | n | n | n | Cloudflare NS server (they can route all traffic via CF at the flip of a switch) |
| codeberg.org | ✅ | Gitea 1.14 customized⚠ | n | n | n | n | Based in Germany; censored an anti-Cloudflare project in a reckless and destructive manner; functions without any JavaScript and the JavaScript that exists is all 1st-party (ref); devs make foolish decisions (improving performance by breaking some browsers, when the performance improvement only affects those they broke.) |
| git.sdf.org | ✅ | Gitea 1.14.1⚠ | n | n | n | n | git.sdf.org censored the deCloudflare project without warning, reason, or recourse. So git.sdf.org apparently unwelcoming of projects driven by privacy, netneutrality, or anti-tech-giant types of activism. Performance is sluggish and the website often times out (perhaps because SDF is also tar-pitting many Tor IPs in defense of attack & it's unclear if this is a temporary measure); SSH over Tor broken but HTTPS over Tor works; some UTF-8 emoticons apparently broke in upgrade from 1.13.1 to 1.14.1. |
| git.shivering-isles.com | ❌ | Gitlab (CE) | n | n | n | n | Cloudflare NS server (they can route all traffic via CF at the flip of a switch); Registration is open but broken-- requires 2FA using a device that can QR-scan, and the email verification link is DoA: 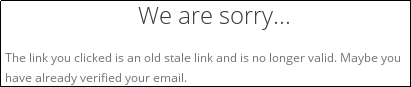 That stale link error triggers even when accessed immediately. That stale link error triggers even when accessed immediately. |
| git.hardenedbsd.org | ✅ | Gitlab (EE) | n | n | n | n | Cloudflare NS server (they can route all traffic via CF at the flip of a switch); possibly restricted to BSD efforts |
| source.puri.sm | ✅ | Gitlab (EE) | n | n | n | n | open registration but activity is restricted to puri.sm efforts; accounts are subject to spontaneous unjustified bans (apparent censorship):  ; no CAPTCHA (confirmed March 2021); is the JavaScript non-free with the enterprize edition? ; no CAPTCHA (confirmed March 2021); is the JavaScript non-free with the enterprize edition? |
Blacklist
These forges have severe ethical or trust issues and should be boycotted:
| forge | registration publicly open | software | Tor-hostile | Cloudflare MitM | forced re/hCAPTCHA | forced execution of non-free software | notes |
|---|---|---|---|---|---|---|---|
| github.com | ❌ (exclusive walled garden) | y | n | n | ☣ | access granted or denied based on national origin; copious ethical issues | |
| sourceforge.net | ❌ (exclusive walled garden) | n | n | n | ☣ | access granted or denied based on national origin; Important site functionality does not work without non-free JavaScript | |
| bitbucket.org | ✅ | Bitbucket Server | n | n | n | ☣ | Amazon AWS-hosted; needs non-free javascript that clusterfucks uMatrix; has some relationship with Netlify; access to source code restricted |
| libregit.org | ❌ | Gitea | n | y | n | n | reg by invite only |
| git.openprivacy.ca | ❌ (exclusive walled garden) | Gitea 1.12.4 | y | n | n | n | Tor users get 404 - suspected botnet; listed as a Cloudflare supporter |
| git.feneas.org | ✅ | Gitlab (CE) | n | n | ⚒ | ☣ | reCAPTCHA impedes registration and imposes non-free s/w |
| gitlab.freedesktop.org | ✅ | Gitlab (CE) | n | n | ⚒ | ☣ | possibly restricted to Freedesktop efforts; reg. blocked by reCAPTCHA |
| salsa.debian.org | ✅ | Gitlab (CE) | n | n | ⚒ | ☣ | forced h/reCAPTCHA; possibly restricted to Debian efforts; serves as an alternative to Debian's email-only bug tracker |
| gitlab.com | ❌ (exclusive walled garden) | Gitlab (EE) | n | y | ⚒ | ☣ | flagship instance running the Enterprise Edition; uses both hCAPTCHA & reCAPTCHA; heavily restricted with discriminatory policies; copious ethical issues |
⚠ Gitea versions note: Gitea 1.14.0 breaks emoji in some browsers. The developers believe that by not supplying fonts to the web visitors who need them, they are improving server performance. Of course the server load is only reduced when talking to a browser that does not have the needed fonts. The idiots could also simply arbitrarily deny service to users at random to get a performance increase. Obviously they have misunderstood the point of performance in the first place: availability!
The best Gitea version ATM is 1.13.7 which opendev.org runs.